
SIM cards are at the heart of mobile network security. Vulnerabilities including the 2013 remote applet installation hack and the recent ‘Simjacker’ vulnerability put millions of users at risk. We wanted to understand the extent to which users need to worry about Simjacker and create ways to know whether your SIM is vulnerable or even under attack.
Key takeaways
- Around 6% of 800 tested SIM cards in recent years were vulnerable to Simjacker
- A second, previously unreported, vulnerability affects an additional 3.5% of SIM cards
- The tool SIMtester](https://opensource.srlabs.de/projects/simtester) provides a simple way to check any SIM card for both vulnerabilities (and for a range of [other issues reported in 2013)
- The SnoopSnitch Android app warns users about binary SMS attacks including Simjacker since 2014. (Attack alerting requires a rooted Android phone with Qualcomm chipset.)
- A few Simjacker attacks have been reported since 2016 by the thousands of SnoopSnitch users that actively contribute data (Thank you!)
Research approach
SRLabs researchers investigated the SIM hacking possibilities from two perspectives: Checking how many SIMs are vulnerable, and monitoring how many are actively being exploited.
Measuring SIM cards
Since publishing the tool SIMtester in 2013 the SRLabs mobile security research team collected and analyzed deep measurements for over 800 SIM cards. Many of these were contributed by community members.
These measurements include details on which applets are installed on the cards, including the “S@T” applet that is targeted by Simjacker. SRLabs discovered a second applet, called Wireless Internet Browser (WIB), that exposes similar functionality. This applet also allows for Simjacker-style attacks.
Each applet on a SIM card is configured with a corresponding minimum security level (MSL). It describes what security features have to be enabled in SMS attempting to send commands to the applet. Attackers can only exploit applets where the MSL was set to zero.
From our collection of 800 SIM card measurements we could infer:
- 9.4% of the tested SIMs have the S@T applet installed
- A subset of 5.6% are vulnerable to Simjacker, because their protection level was set to zero
- 10.7% have the WIB applet installed
- A subset of 3.5% are vulnerable to a Simjacker-style attack against the WIB applet
- In total, 9.1% of tested SIM cards were vulnerable to attacks against either S@T or WIB
To test your own SIM card for vulnerability to these and other attacks using SIMtester, please refer to the FAQ below.
Detecting attacks on SIM cards
In 2014, the SRLabs team published a mobile self defense tool: SnoopSnitch. Among other attacks, SnoopSnitch detects attacks based on suspicious binary SMS including Simjacker.
SnoopSnitch has attracted more than 500,000 users. A subset of these users run SnoopSnitch on rooted Android phones with Qualcomm chipset, which is a precondition for detecting binary SMS attacks:
We received reports from 8 users about 29 OTA SMS targeting the S@T applet The first message was reported in 2016 Most of the messages targeted users in Latin and South America To monitor your phone for Simjacker and other attacks using SnoopSnitch, please refer to the FAQ below. Kindly note that SnoopSnitch alerting requires a rooted phone, which comes with its own set of security concerns.
Remote SIM card attack recap
To fully understand the SIM vulnerabilities, we should first discuss how binary SMS “over-the-air” (OTA) protocols work for SIMs.
SIM cards are small computers inside your mobile phone. Besides their main role of authenticating you to the network, they run Java applications and can instruct your mobile phone to do various things:
- Make a call
- Send an SMS
- Get surrounding cell-IDs (location)
- Prompt the user for input
- Establish a TCP/TLS connection
- Open a browser on a specific URL
Applications on the SIM card can be remotely steered by operators sending a special class of SMS: the so called “OTA SMS” (class 2, binary SMS). Common remote operations are installing, updating, or removing an application, change file contents, perform secure authentication involving users for (e.g.,) banking.
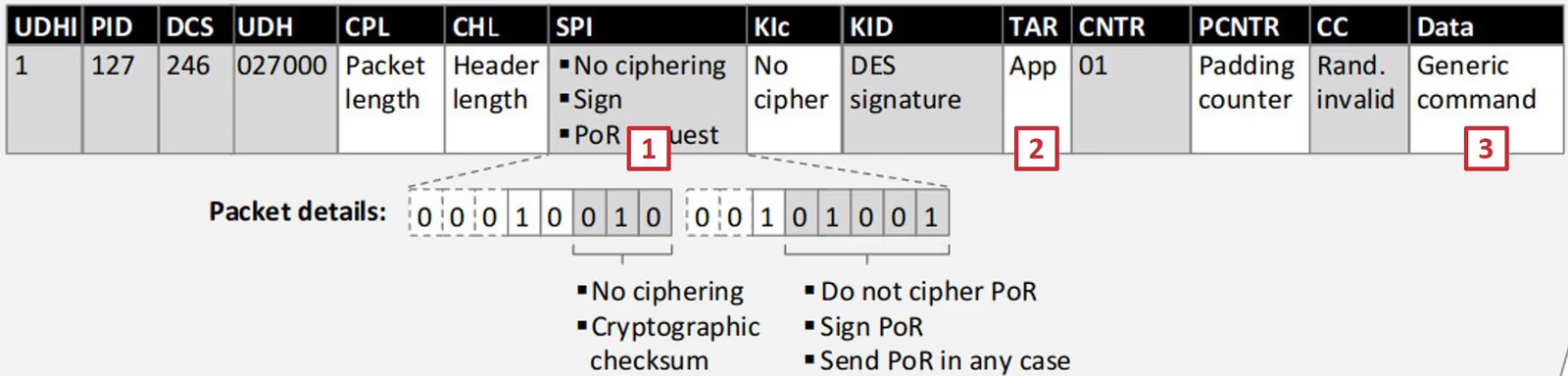
The “TAR” (Toolkit Application Reference) field (2) of an OTA SMS indicates what SIM card application the command (3) is intended for. For security reasons, messages from/to SIM applications can be encrypted and integrity protected. The “SPI” (Security Parameter Indicator) field (1) defines what protections are used in the SMS. Respectively, on the SIM card, the security settings describe on a per-application basis what SPI security levels have to be met by the SMS attempting to control the application. They can also be completely disabled, allowing unsigned and unencrypted SMS to access an application. SRLabs research found that SIM cards from multiple vendors could be abused – for example for location tracking – because of implementation bugs and poor security configurations, [as reported in 2013].
An MSL (Minimum Security Level) is associated to each installed applet by vendor/operator. If the MSL is set to zero, the SIM card accepts messages without performing any security check, resulting in unrestricted access to the application. SIM cards with misconfigured security settings have been discovered in 2013 and now appear again according to the Simjacker findings from AdaptiveMobile.
SIM attack mitigation
Mobile network operators can address the SIM security issues in two ways: By removing the SIM applet vulnerabilities, or by blocking binary SMS on their networks. Both approaches come with limitations, and a combination of both is recommended as best practice.
These are the same recommendations given by the GSMA and by SRLabs in 2013 and implemented by many, but not most, mobile networks, since then.
Users cannot easily protect themselves in the same way since SMS delivery and SIM configuration are outside of their control. Users can however check whether a SIM is vulnerable, using the SIMtester tool, or whether they are being attacked, using SnoopSnitch running on a rooted Android phone. Details on both tools are provided below.
FAQ
Is my SIM card vulnerable [SIMtester]?
In short: Unlikely.
To be vulnerable, the following conditions have to be met:
- An application with abuse-potential is present on the SIM card (e.g. S@T or WIB)
- The MSL of the application is set to zero
- The provider forwards binary SMS In the wake of the 2013 research results, SIM vendors and mobile operators worked together to reduce the risks related to SIM card attacks.
None of the most recent SIM cards we tested show the presence of the vulnerable applications or badly chosen security settings.
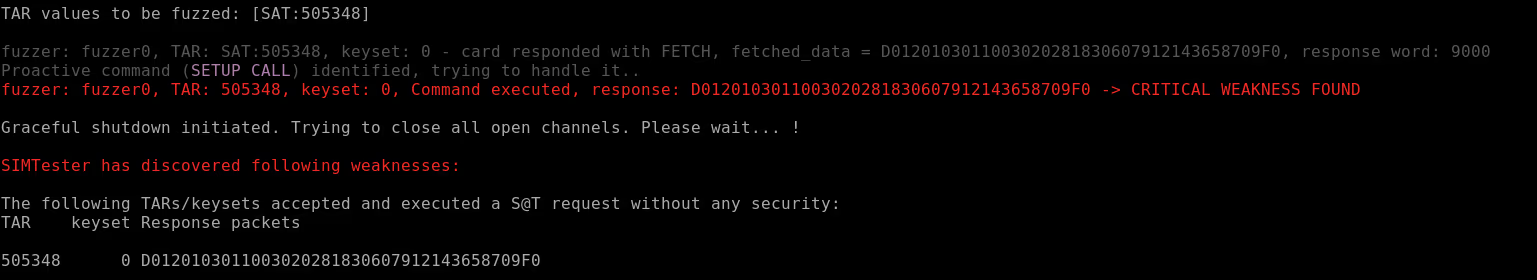
You can test your own SIM card for vulnerability to these and other attacks using SIMtester. To do so you need a compatible smart card reader [^1] and execute the following command:
java -jar SIMTester.jarIn case the SIM card is vulnerable to Simjacker, the output will look like the following:
Is my SIM card under attack [SnoopSnitch]?
Again: Very unlikely, based on past SnoopSnitch measurements.
You can install SnoopSnitch to monitor for suspicious incoming binary SMS. For the network attack detection features to work, you need to have a rooted Android phone with a Qualcomm chipset.
With our open source app Snoopsnitch you are able to detect these exploitation attempts targeting your SIM card. Exploitation is performed by sending a binary SMS to your phone. In case such a message arrives, SnoopSnitch warns you with an even in the “SMS & SS7 attacks” .
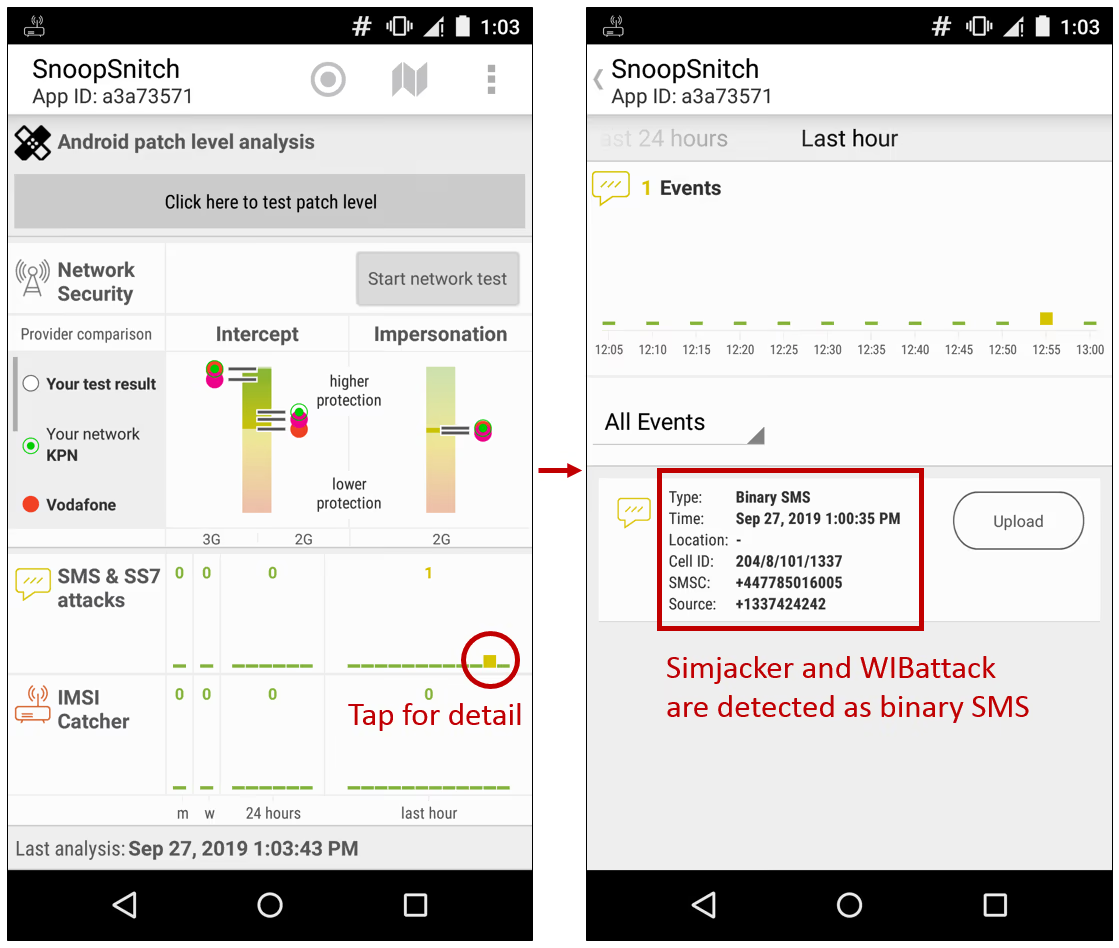
You can submit the message contents to us for further analysis and confirmation of what happened.
- You can download [SnoopSnitch%20from%20the%20Android%20Playstore.%20Further%20details%20on%20its%20use%20and%20functionality%20is%20available%20in%20the%20SnoopSnitch%20wiki]
- A rooted Android phone with a Qualcomm chip is needed for the SMS attack alerting feature
Credits
We would like to thank Lakatos, security researcher at Ginno Security Lab, for his support in creating proof of concept payloads needed for the SIM card analysis.
[^1] PC/SC-compatible SIM card readers: SCM SCR-3310 and HID Omnikey 3121