Key takeaways
- Due to Qualcomm’s proprietary architecture, a lack of security tooling exists around their baseband.
- Our tooling enables research on Hexagon baseband with significantly reduced engineering work.
- We release the first open-source toolchain for full-system emulated Hexagon firmware fuzzing at TROOPERS25.
Overview
Every phone has a cellular baseband processor to handle mobile communications (5G, 4G, GPS, and more).
Qualcomm created a specific architecture for its baseband called Hexagon. It powers the baseband processors found in most leading smartphones, including every iPhone since generation 12 except iPhone 16e and all Snapdragon-based devices. This architecture, being different from the classic ARM, x86, or MIPS that we all know, leads to a lack of security research. Most of the produced tooling is simply not applicable to it!
We developed the first open-source toolchain for full-system emulated fuzzing of any Hexagon firmware. Our work addresses a gap in baseband security research by making a previously inaccessible attack surface available for analysis. With our toolchain, open-sourced here, we invite the community to collaborate and build upon this work.
Previous research landscape and the Hexagon gap
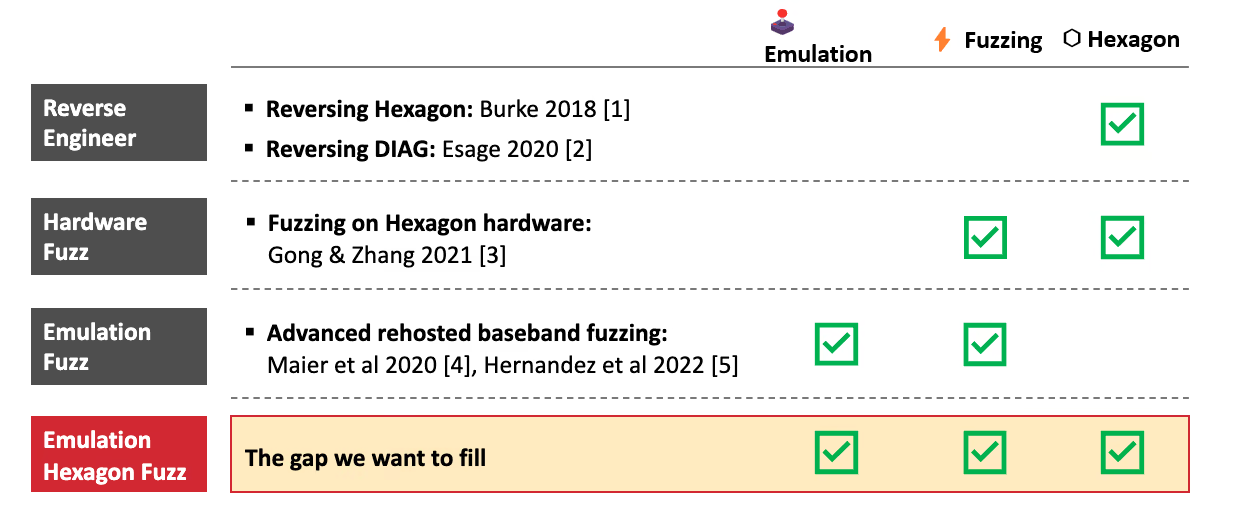
The baseband security research community has made considerable progress in recent years, yet a critical gap has persisted regarding Qualcomm’s Hexagon architecture.
Early work like BaseSAFE (2020, Maier and al.) introduces an advanced framework for fuzzing basebands. Building on this, FirmWire (2022, Hernandez et al.) provides baseband emulation platforms for fuzzing.
These tools are the go-to solution for fuzzing basebands which use ARM, x86, MIPS and other standard architectures. But, as the FirmWire paper observes:
“Unlike other baseband implementations, Qualcomm leverages a fully-custom architecture known as Hexagon […] Unfortunately, tooling for this architecture is sparse, and especially full-system emulators are lacking.”
Other research efforts around Hexagon are limited to specific aspects, such as DIAG protocol analysis and reverse engineering (see Figure 1).
Challenges
Hexagon presents several barriers that make firmware analysis challenging:
- Custom CPU architecture: Most tooling lacks support, making reversing challenging.
- Custom OS and software stack: Requires adapting common attack techniques.
- Custom communication protocols: No free tools or documentation exist.
The primary challenge in reversing Hexagon baseband lies in the lack of tooling support. Ghidra, IDA, and similar tools do not support the architecture out of the box, and while QEMU offers user-space emulation for Hexagon, full system emulation remains unavailable.
FirmWire, for example, relies on QEMU for emulation and introspection. Since Hexagon does not yet have proper full-system Hexagon emulation in QEMU, it is not possible to use it for analysing this firmware, as explained in the quote above.
Solution
To address these challenges, we used a QEMU fork from the Qualcomm Innovation Center (QuIC) supporting Hexagon full-system emulation. With the addition of LibAFL’s QEMU fork, we built a custom fuzzing and reverse engineering tool tailored for Hexagon.
1. How we merged QuIC/QEMU with LibAFL’s QEMU
The QEMU fork from QuIC includes a hexagon_sysemu branch that, with minor modifications, can successfully boot iPhone baseband firmware. We adapted this codebase for fuzzing by integrating it with LibAFL’s QEMU. Since the two projects share no common ancestor in Git, merging them requires significant manual effort and custom fixes.
We share our QEMU fork in this repository, which can be used directly. Like QuIC’s fork, you can emulate Hexagon firmware and connect LLDB if you have Qualcomm’s Hexagon SDK. You can also compile it as a library and connect LibAFL for introspection directly in Rust via its elegant API.
2. How we created a fully coverage-guided fuzzer
Using this approach, we can recreate something similar to FirmWire and use Rust-based hooks for control flow modification. When booting a baseband firmware, these code flow manipulations are necessary. The emulator won’t provide the hardware components that the firmware communicates with.
We created a fuzzer that handles control flow manipulation for a specific iPhone firmware, up to user mode, utilizing these LibAFL bindings. We provide this with a JSON-based approach, where you can set breakpoints with their handlers in the configuration. You can also modify the QEMU command line arguments to debug firmware emulation issues.
{
"breakpoints": [
{
"name": "qurt_println",
"address": "0xfe10f2b0",
"handler": "HandlePrintln"
},
{
"name": "another_println",
"address": "0xc03c96cc",
"handler": "HandlePrintln"
},
]
}Figure 2. Snippet of the JSON-based configuration for Hexagon fuzz
With this tooling, a fully coverage-guided fuzzer can run on any Hexagon-based baseband firmware. This way, all the 5G/4G/GPS stacks from your phone can theoretically be tested for security via a Rust-based API and fuzzed extensively.
To find vulnerabilities, you need to:
- Boot the firmware into the expected state
- Provide a harness that specifies the target function(s) to fuzz within the baseband
3. How we improved reverse engineering through visualized coverage
We also developed a script to visualize the fuzzer’s coverage. It parses QEMU’s debug logs, printing the program counter and coloring it in Ghidra, with different colors per thread. This improves the code comprehension during reverse engineering by providing immediate insight into the fuzzer progress. We heavily used this to advance the boot procedure as it allows dynamic debugging between emulated code in QEMU and disassembly in Ghidra.
We also provide some documentation on how to reverse engineer these basebands and use the tooling.
Architecture overview
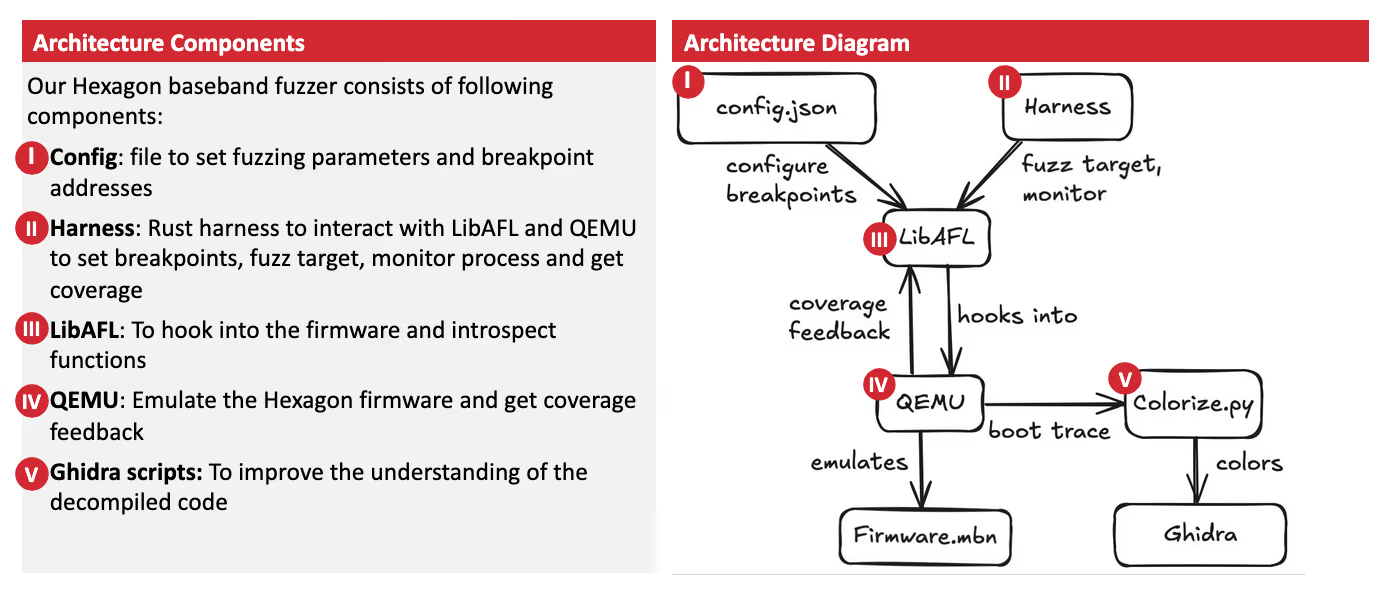
The toolchain enables you to:
- Emulate Qualcomm Hexagon baseband firmware in a controlled environment
- Add breakpoints and modify runtime behavior through Rust hooks
- Skip initialization functions to speed up the boot process
- Instrument common functions like
printffor debugging - Perform coverage-guided fuzzing on baseband components
- Do vulnerability discovery in Hexagon basebands
Current status and next steps
Our current implementation successfully:
- Boots the iPhone baseband firmware, with 100+ lines of boot log output
- Instruments and manipulates the control flow of the firmware
- Provides basic fuzzing infrastructure to analyze Hexagon baseband firmware
Here's how we plan to improve:
- Better target function identification through enhanced reversing
- CLADE/CLADE2 decompression support
- Enhanced fuzzing harness with appropriate parameter initialization
- Integration with dynamic testing from phone/SIM interfaces
This work represents a significant step forward in baseband security research, bridging the gap in Hexagon-based baseband analysis and bringing much-needed transparency to the security posture of these devices.
We presented this research at the Troopers25 conference, (slides available here) which will be available on YouTube in a few weeks. Visit our GitHub repository to check out our fuzzer!
References
- Burke 2018, A Journey into Hexagon
- Esage 2020, Advanced Hexagon DIAG
- Gong & Zhang 2021, In-Depth Analyzing and Fuzzing for Qualcomm Hexagon Processor
- Maier et al. 2020, BaseSAFE: baseband sanitized fuzzing through emulation
- Hernandez et al. 2022, FirmWire: Transparent Dynamic Analysis for Cellular Baseband Firmware


