In 2016, krebsonsecurity.com was hit by a huge DDoS attack. Shortly thereafter, DNS provider Dyn went down, leaving many web applications unreachable. The attacks were driven by the Mirai malware, which created a botnet by searching for and compromising devices found to be running telnet services with default credentials. In 2017, the Reaper malware created a botnet of IoT devices by exploiting a list of known vulnerabilities in web interfaces. Both malwares spread by probing random IP addresses, so only internet-reachable devices had the potential to be hacked and become part of the botnet.
Most remote video cameras, fortunately, are not exposed directly to the internet. However, insecure cloud services put them at a similar risk of becoming part of the next IoT camera botnet.
Cloud protocols bypass firewalls and allow for connections into private networks
This enables viewing remote devices that are in private home networks.
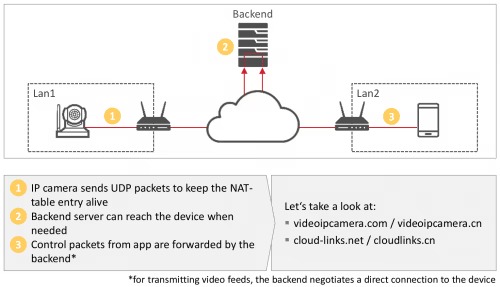
When an IP camera starts, the camera connects to the cloud backend and keeps the connection alive as long as the device is switched on. This allows the camera to be contacted and controlled conveniently via a smartphone app from anywhere in the world.
Two popular backends, videoipcamera.com / videoipcamera.cn and cloud-links.net / cloudlinks.cn have significant security issues at the time of this research in Nov 2017.
List of connected devices can be retrieved from the backend
Device IDs have a length of up to six digits for Videoipcamera and up to seven digits for Cloudlinks. The validity of all device IDs can be checked unauthenticated within one hour via UDP. At the time of testing, there were 140,741 valid device IDs on Videoipcamera and 3,277,280 on Cloudlinks.
Certain types of packets are forwarded by the backend just based on the device ID. This allows for sending packets to all valid devices. A vulnerability in the handling of these packets would open up all devices to efficient exploitation. We did not find such an issue that would expose all devices to hacking, but several smaller issues that expose hundreds of thousands of devices, including the following issues:
Default and weak passwords can be enumerated
By replaying packets with changed device IDs, passwords can be efficiently checked against all devices.
On Videoipcamera, 63,000+ devices (45%) are accessible via the default password 888888 and, based on a random sample, 700,000+ Cloudlinks devices are accessible with the password 123. A demo video is available.
Cloudlinks employs some rate limiting techniques that can be bypassed easily. Without factoring in weak user-choosen passwords, the cloud backends expose a total of 763,000+ devices with default credentials.
Remote exploitation can be automated
To demonstrate the problem posed by this large number of accessible devices, we developed a remote exploit for Videoipcamera devices. First, the network settings are queried and the DNS server changed to redirect the device’s update requests. Then, a firmware update is initiated and a malicious firmware delivered. A demo video is available.
As the firmware is only protected by an MD5 checksum that ís encrypted with a static DES key, creating a malicious firmware is relatively easy. This attack allows for remote command execution on all Videoipcamera devices for which credentials are known.
Premium vendors share similar problems
The market leader Hikvision shares some of the same problems: Hikvision device IDs are longer, but not long enough to prevent enumeration. Based on a random sample of 100,000 IDs, we estimate there are 2,760,000 valid devices of which 50,000 have the default password ABCDEF that is set when a non-cloud device is upgraded to cloud connectivity. Research by Jake Reynolds showed that the FLIR cloud service by Lorex, yet another vendor, allows direct tunneling across firewalls to arbitrary ports on the camera, just based on device ID. Subsequently, this allowed exploiting a known authentication bypass in the device’s web interface.
Network camera vendors need to improve cloud service security The security of IP camera cloud services mainly relies on obfuscation through proprietary protocols. Large numbers of cloud-exposed devices in private networks will certainly capture the interest of bot herders, exposing users to privacy intrusions, and intrusions of their private networks; and exposing the internet to large-scale DDoS attacks. The internet should brace itself for ever-larger DDoS as insecure devices are unlikely to disappear anytime soon. Details were presented at DeepSec on Nov 16 2017: Announcement](http://blog.deepsec.net/deepsec-2017-talk-next-gen-mirai-botnet-balthasar-martin-fabian-braunlein/) and [slides.

