
We investigated a sprawling criminal e-commerce network that operates fake webshops. The fake shops processed over a million orders with an aggregate order volume of USD 50 million over the past three years.
Key Takeaways
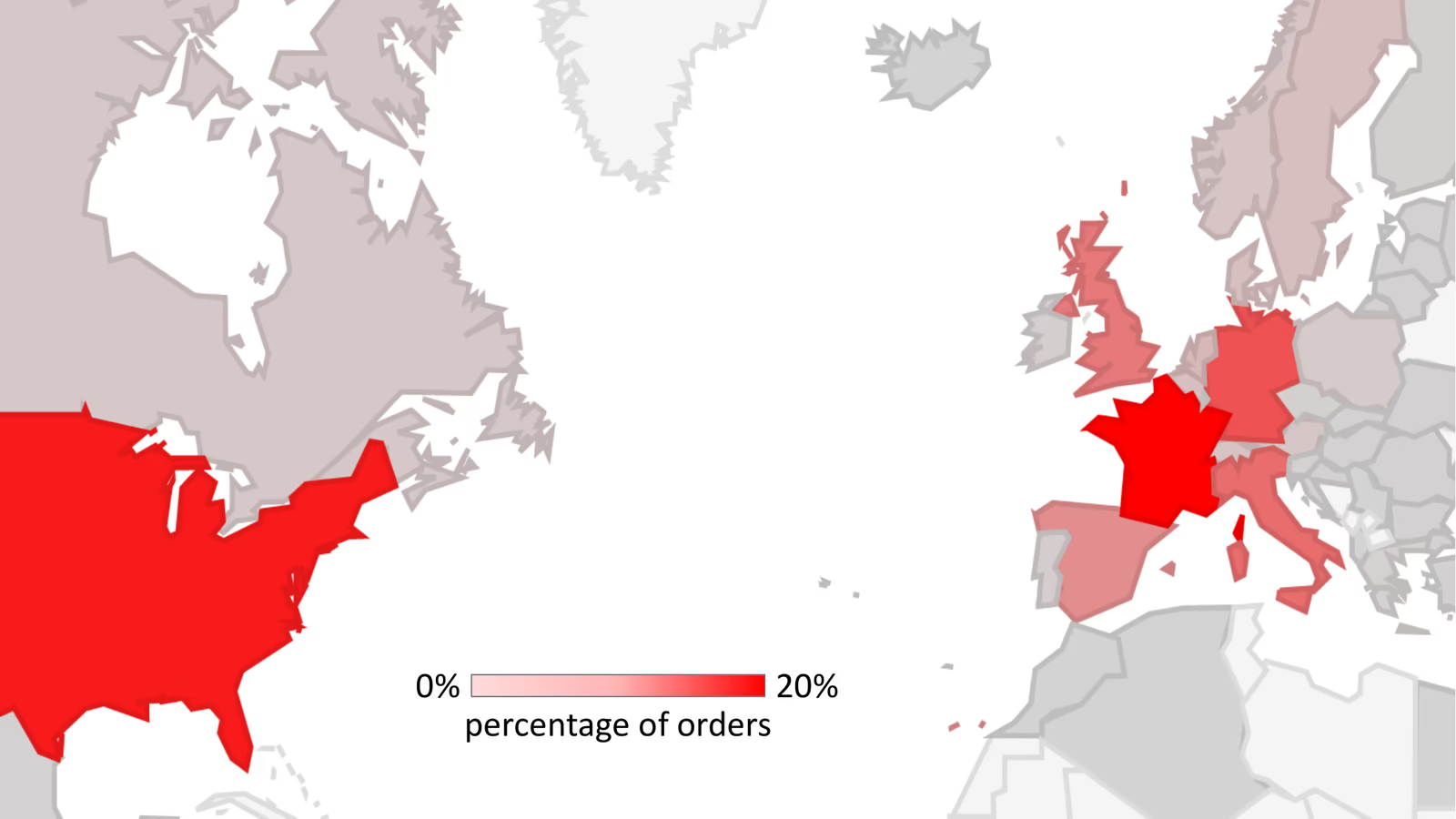
A criminal network operates tens of thousands of fake webshops, frequently leveraging previously expired domains with good Google reputation Victims access BogusBazaar shops hoping for deals on shoes and apparel, but get their credit card details stolen instead Over 850,000 customers have already fallen victim, mostly from Western Europe and the USA; and almost none from China, the main operating hub of the fraudsters When ordering online, a deal that sounds too good, probably is. Services like Fakeshop Finder [German] help consumers check if webshops are legitimate
Fraud Impact
A criminal group, which we name BogusBazaar, operates an extensive network of 75,000+ domains hosting fraudulent webshops. As of April 2024, approximately 22,500 domains were active. The network has processed more than one million orders since 2021, with an estimated aggregate order volume exceeding USD 50 million.
Not every order results in successful payment, so the actual primary financial damage is lower. Secondary damages caused by fraudulent use of stolen credit card details add to the overall damage.
Our research is covered by Die Zeit (German), The Guardian (English), and Le Monde (French). A subset of this criminal network has previously been reported on by Yarix.
Fraud Method: Fake shops harvest credit cards and steal funds
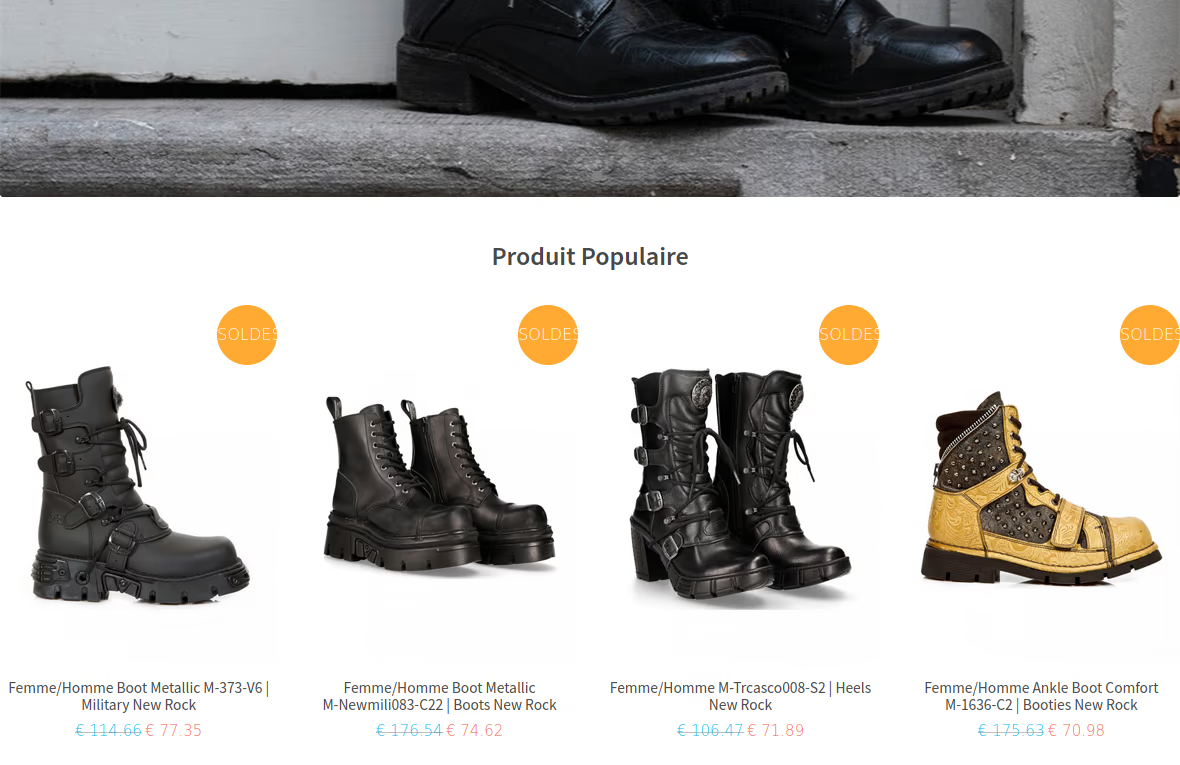
BogusBazaar lures victims onto fake webshops, mainly offering shoes and apparel by well-known brands at low prices. BogusBazaar pursues two crime methods in parallel:
- Credit card harvesting. Fake payment pages collect victims’ contact and credit card details
- Fake selling. Fake shops initiate payments for expensive merchandise. In most cases, the victims do not receive any merchandise. Occasionally, they receive cheap counterfeits. Payments are facilitated through PayPal, Stripe, and credit card processors
Both methods are sometimes used against the same victim in sequence: First, credit card data is harvested through a spoofed payment interface. The victim is then shown an error message and forwarded to a functioning payment gateway, which initiates a payment.
Organizational Structure: Fraud-as-a-Service
The group has adopted an ‘infrastructure-as-a-service’ model: A core team is responsible for infrastructure management, while a decentralized network of franchisees operates fraudulent shops.
The BogusBazaar core team deploys infrastructure and appears to operate only a small number of fake webshops. The core team is responsible for developing software, deploying backends, and customizing various WordPress plugins that support fraud operations.
Franchisees manage day-to-day operations of fake shops running on this shared infrastructure. Research indicates that a large part of the network operates from China.
Technical Setup: Automation and orchestration at scale
The criminals operate webshops, payment gateways, and management applications on separate infrastructure.
Frontend
BogusBazaar primarily uses previously expired domains and prefers domains with good Google reputation. Shops are created semi-automatically with customized names and logos. Quality assurance procedures aim to minimize inconsistencies.
Webshops currently run on the WooCommerce WordPress plug-in. Past versions of fraudulent webshops also utilized Zen Cart and OpenCart.
Payment pages can be rotated without changing the store fronts, for instance when a payment page is blocked for fraud.
Backend
A typical BogusBazaar server runs about 200 webshops, with few servers hosting more than 500. These servers are often associated with more than a hundred IP addresses each. Externally, the webshops are exposed via Cloudflare. Most servers are hosted in the United States.
Over time, the group has increased the level of infrastructure automation. Today, extensive orchestration capabilities enable BogusBazaar to quickly deploy new webshops or rotate payment pages and domains in response to take-downs.
Conclusion and Contact
The criminal network has grown for years through low-key highly-scalable fraud. Our insights enable network infrastructure operators, payment providers, and search engines to identify the crime nucleus and prevent future large-scale abuse.
SRLabs shared research findings with relevant stakeholders including authorities. Some of the fake shops are now offline.
Please send questions about this research to: bogusbazaar@srlabs.de