








We released an all new version of our mobile anonymity software package “blue-merle.” This software package for the GL.iNet Mudi 4G LTE router adds additional privacy protections to mitigate some deanonymization risks exhibited by the original product.
The latest version improves anonymity and user experience. Most notably, it adds compatibility with the latest firmware version (v4.3.8) and supports the latest hardware generation (Mudi v2 based on the EM050-G modem).

What’s new in blue-merle 2.0?
The update brings enhanced privacy, better user experience and integration, and an offline installation option.
- Enhanced Privacy: The updated package also randomizes the Mudi’s MAC address used for Wi-Fi uplink in repeater mode.
The first version of blue-merle already randomized the MAC address and BSSID the Mudi used for its Wi-Fi connections to clients on each boot. However, this MAC address randomization was not effective when using an existing Wi-Fi network as uplink. Version 2.0 closes this gap and implements MAC address randomization in repeater mode by updating the glconfig.general.macclone_addr setting via the uci set command.
- User experience and integration improvements: Numerous improvements to the code base ensure a smoother and future-proof experience for all users.
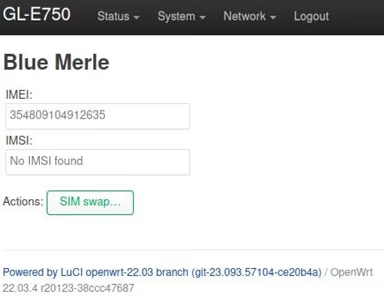
While the original release was mostly a collection of scripts that were copied to the device and invoked in non-standard ways, this release offers blue-merle as a standard package that can be installed with the Mudi package manager. The package now also includes a LuCI web interface that allows the user to initiate a SIM swap and IMEI change.
- Offline Installation: Users can now install blue-merle without ever connecting their Mudi to the internet, further catering to the needs of privacy-conscious users.
Blue-merle relies on several software dependencies that need to be installed on the Mudi before the package can be used. The default installation method automatically ensures dependencies are installed by using the official OpenWRT package manager opkg. For version 1, this required the router to be online without the privacy protections offered by blue-merle.
This release adds an offline installation method in which the release artifacts can be acquired in advance and installed to the Mudi via scp and ssh. This ensures that blue-merle is active before the Mudi is ever connected to a 4G or Wi-Fi uplink. See the documentation for instructions for the offline installation.
Where can I get blue-merle 2.0?
Grab the latest release binaries from our GitHub repository. We’ve also provided detailed instructions on how to compile the code yourself and included a comprehensive user guide to help you get started.
The recommended online installation method consists of five simple steps:
- Ensure that the Mudi firmware is running 4.3.8. Update via the official channels if necessary.
- Download the latest blue-merle release IPK file from GitHub.
- Copy the IPK file to the Mudi via
scp. - On the Mudi: Update the local package database via
opkg update. - On the Mudi: Install the package via
opkg install blue-merle*.ipk.
For further details, check out the installation instructions in the project README.
Disclaimer and call for action
Users should use blue-merle at their own risk and only if they understand what it does and does not do for them. While blue-merle improves the anonymity and reduces traceability of a GL.iNet Mudi 4G LTE router by addressing the privacy gaps of the stock firmware (as described in our whitepaper), the actual level of anonymity it offers depends on other factors.
The blue-merle project does not provide any protection against user error or improper implementation. Firstly, blue-merle permanently removes all traces of the router’s old identity. However, any resulting privacy benefits depend on the degree of anonymity of the used SIM card and the used IP anonymization technology (VPN/Tor). In some countries, anonymous SIM cards may be difficult to acquire. Secondly, blue-merle can lead to issues when changing the router’s identifier to an IMEI that is also active within the same network or to the IMEI of a stolen device. Depending on your jurisdiction, changing your IMEI might violate local regulation or law. Finally, blue-merle is a research project and further or unanticipated modifications to the Mudi router can significantly impact its effectiveness.
For more information on our research and consultancy work within the mobile network field, check out more of our research blog posts or consider joining our team of technical experts.
